Acronis Cyber Protect 、Backup 、and Recovery Solution
1. Security gaps and vulnerability assessments with #CyberFit Score
2. Data loss prevention (DLP) with device control
3. Exploit prevention: Behavior-based detection heuristics prevent the exploitation of unknown vulnerabilities, including memory exploits and injections
4. Remote desktop and remote assistance、Automated patch management – close vulnerabilities before they’re exploited
5. Drive health monitor: Proactively mitigate downtime caused by drive failure with predictive monitoring and alerts
6. Continuous data protection (CDP): Acronis’ agent monitors and backs up changes in real-time for with near-zero RPOs, ensuring no data is lost
7. Expanded backup support: Covers Microsoft SQL clusters, Microsoft Exchange clusters, Oracle DB, and SAP HANA
8. Data protection map and compliance reporting: Scan clients’ environments to ensure their workloads, files, applications, and users are protected
Advantages of Sajet MES Integration
1.
Automated encryption for Manufacturing Execution System related information
2.
Instant recovery for MES software applications with Antivirus and Antimalware protection
3.
Unified software security management through MES management platform
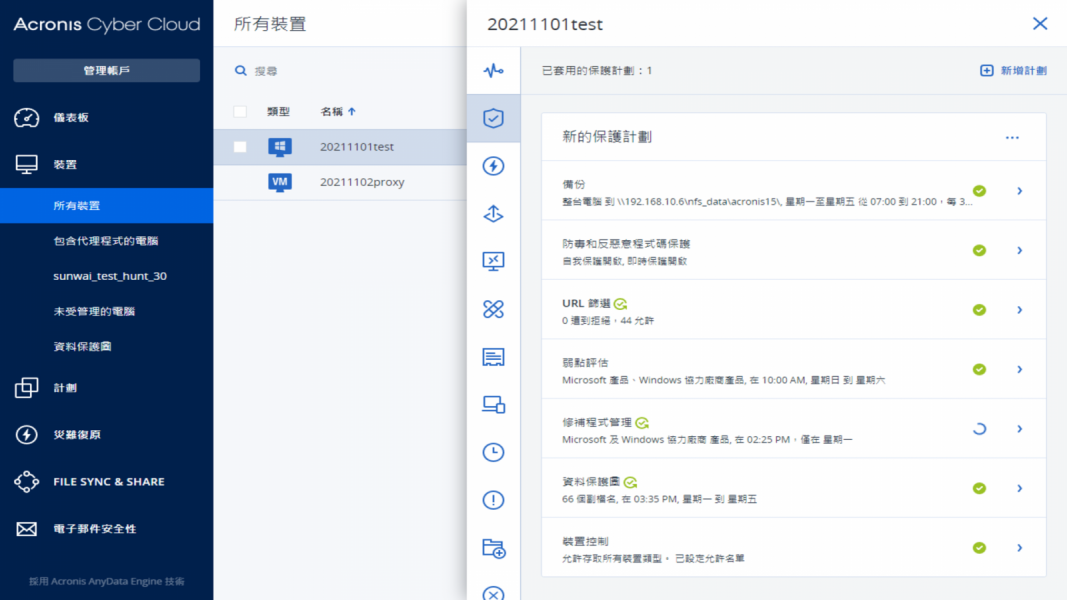
Figure 1. System Interface
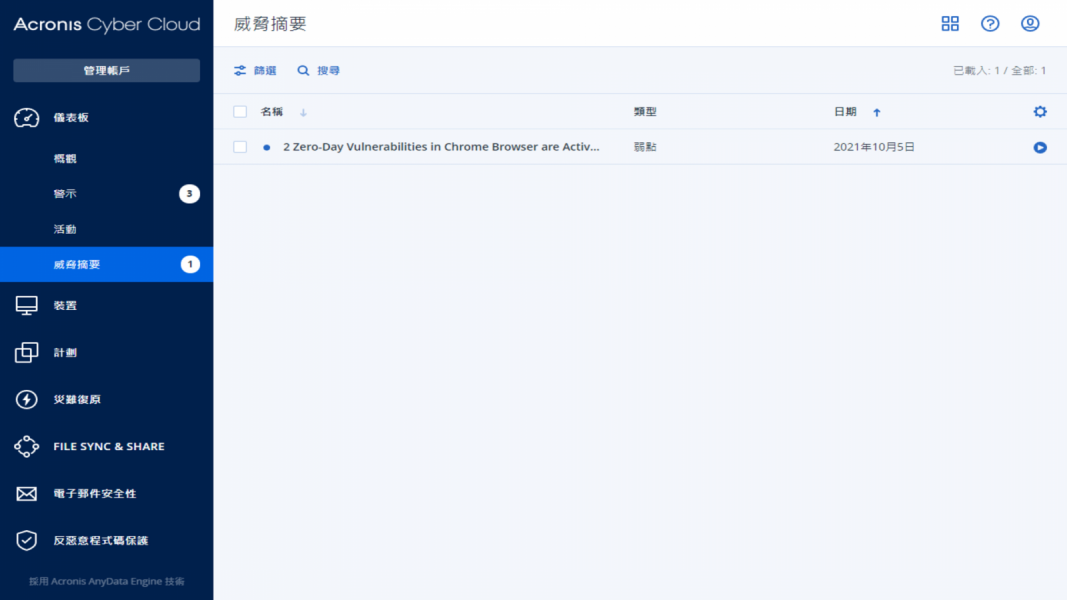
Figure 2. System Interface



